This guide supports the Cloud Network Firewall (CNFW) mini-test, which compares the security effectiveness of native firewall solutions from Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
This guide should supplement what vendors already provide to their customers. Please see the links below for the best practices and guides for each product we tested. We have also included information for Keysight’s CyPerf v5.0 software testing platform, enabling enterprises to easily replicate our results.
Cloud Network Firewall Test Topology

AWS Network Firewall
Product, best practices, and documentation:
- AWS Network Firewall: https://aws.amazon.com/network-firewall/
- What is AWS Network Firewall? : https://docs.aws.amazon.com/network-firewall/latest/developerguide/what-is-aws-network-firewall.html
- AWS Network Firewall Documentation: https://docs.aws.amazon.com/network-firewall
Following AWS’s documentation, the CyberRatings team deployed the AWS Network Firewall instance in routing mode to inspect both inbound and outbound traffic. We set up and configured our threat testing harness using CyPerf, which was installed using the AWS Marketplace.
Deployment Steps:
- Route Tables: The route tables must be configured to properly route traffic across the AWS Firewall (AWS FW). Three necessary routing tables are required, and they are described below.
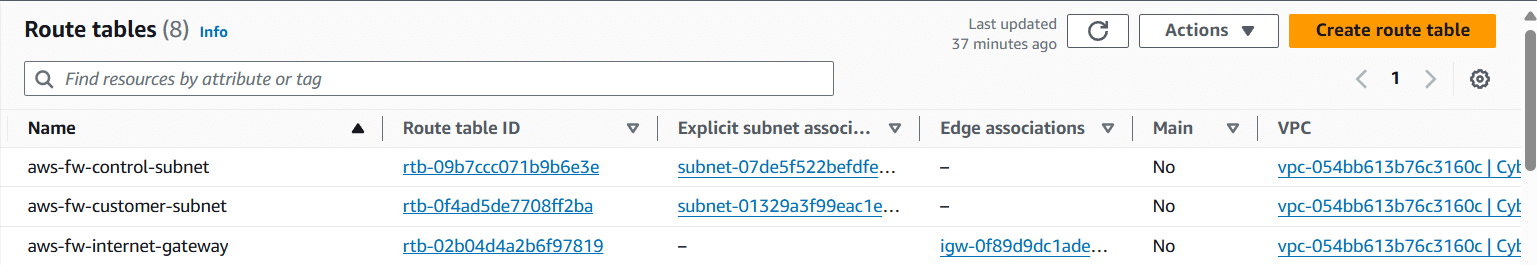
- Control Subnet: routes traffic from and to the Control Subnet, the subnet on which the AWS FW endpoint has been deployed.
- Customer Subnet: routes traffic from and to the Customer Subnet, which is the subnet on which the trusted clients and servers are deployed, i.e., the LAN side of the Firewall.
- Public Internet Gateway: routes traffic from and to the Customer Subnet, which is the subnet on which the trusted clients and servers are deployed, i.e., the WAN side of the Firewall.
- Firewall Policies: create rule groups for various traffic types, including allowed and blocked IPs and protocols.
- Firewall Subnet: configure in each VPC to direct traffic through the firewall.
- Logging & Monitoring: Lastly, we enabled logging to store data in CloudWatch for auditing and monitoring purposes (S3 can also be utilized).
For AWS Network Firewall, multiple steps are required:
- Enable logging (both flow and alert logs)
- Forward logging output to one or more AWS services (CloudWatch, S3 Storage, etc.)
- Then, we analyzed the logs (in JSON format). They can also be exported to multiple formats to be viewed locally.
CyPerf: We used AWS Marketplace and installation was straightforward.
Google Cloud NGFW Enterprise Firewall
Product, best practices, and documentation:
- Product Overview: https://cloud.google.com/security/products/firewall?hl=en
- Threat Signatures Overview: https://cloud.google.com/firewall/docs/about-threats
- Threat Signatures: https://cloud.google.com/firewall/docs/about-intrusion-prevention#ips-threat-signatures
- Configure Intrusion Prevention Service: https://cloud.google.com/firewall/docs/configure-intrusion-prevention
- Network Firewall Policies: https://cloud.google.com/firewall/docs/network-firewall-policies
- Network Firewall Policies and Rules: https://cloud.google.com/firewall/docs/use-network-firewall-policies
- Firewall Rules: https://cloud.google.com/firewall/docs/firewall-policies-overview#pre-defined-rules
We followed their best practices and documentation and deployed the instance in routing mode to inspect both inbound and outbound traffic. We set up and configured our threat testing harness using CyPerf. Using the provided instructions and documentation, it was easy to deploy.
Cloud NGFW’s threat detection and prevention capabilities are powered by Palo Alto Networks threat prevention technologies[1]. To help protect your network, Cloud NGFW supports a default set of threat signatures with predefined severity levels. Users can view all the threat signatures configured in Cloud NGFW in the threat vault.
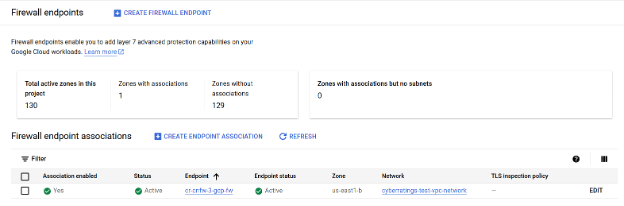
Firewall Endpoints:
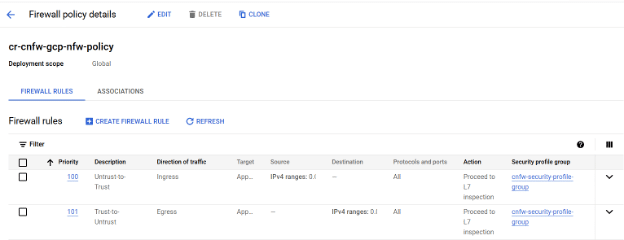
Firewall Policy:
CyPerf: The CyPerf agents were deployed on GCP using Terraform. The procedure for deploying using Terraform is shown below.
Installation of Google Cloud Software Development Kit (SDK):
- Reference: Install the gcloud CLI | Google Cloud CLI Documentation
- Next step: https://github.com/Keysight/cyperf/tree/main/deployment/gcp/terraform
- Once the GCP SDK has been installed successfully, install the agents using Terraform. (These were obtained from Cyperf): https://github.com/Keysight/cyperf/tree/main/deployment/gcp/terraform
Microsoft Azure Firewall Premium
Product, best practices, and documentation:
- Product Overview: https://azure.microsoft.com/en-us/products/azure-firewall/?msockid=229c658bd99a6adf2a0c71fcd8176bc3
- Azure Firewall Premium: https://learn.microsoft.com/en-us/azure/firewall/overview#azure-firewall-premium
- Azure Firewall documentation: https://learn.microsoft.com/en-us/azure/firewall/
- Azure Firewall’s Threat Protection: https://techcommunity.microsoft.com/blog/azurenetworksecurityblog/exploring-azure-firewalls-threat-protection/3869571
We followed their best practices and documentation for Microsoft Azure Premium Firewall and deployed the instance in routing mode to inspect both inbound and outbound traffic. We set up and configured our threat testing harness using CyPerf.
Microsoft Azure Firewall Premium uses Microsoft’s closed-source signatures. As of October 2024, its ruleset contained over 67,000 rules in over 50 categories.
Deployment Steps:
- First, we installed Terraform: https://learn.hashicorp.com/tutorials/terraform/install-cli
- Then we installed Azure CLI: https://learn.microsoft.com/en-us/cli/azure/install-azure-cli
- Firewall Policy:
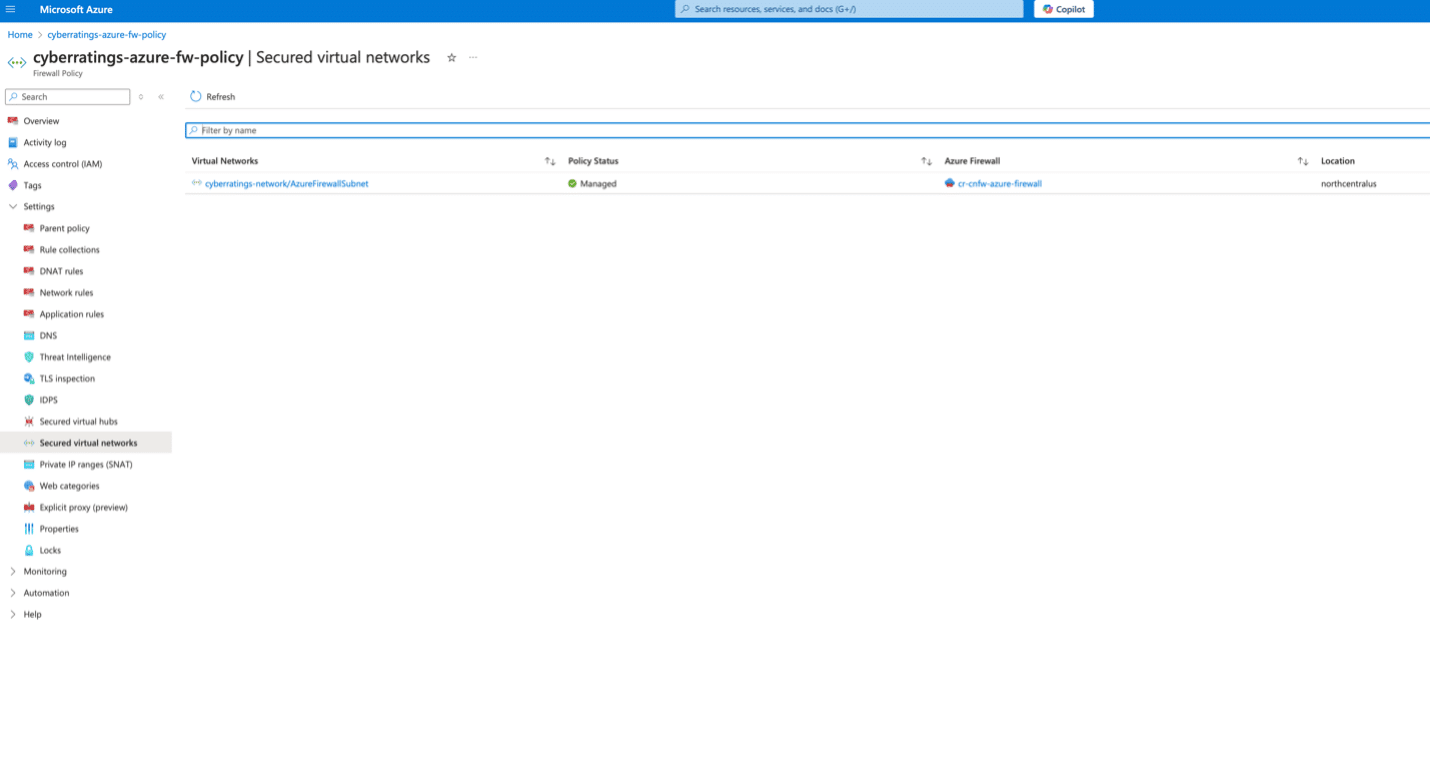
- Firewall IDPS Policy:
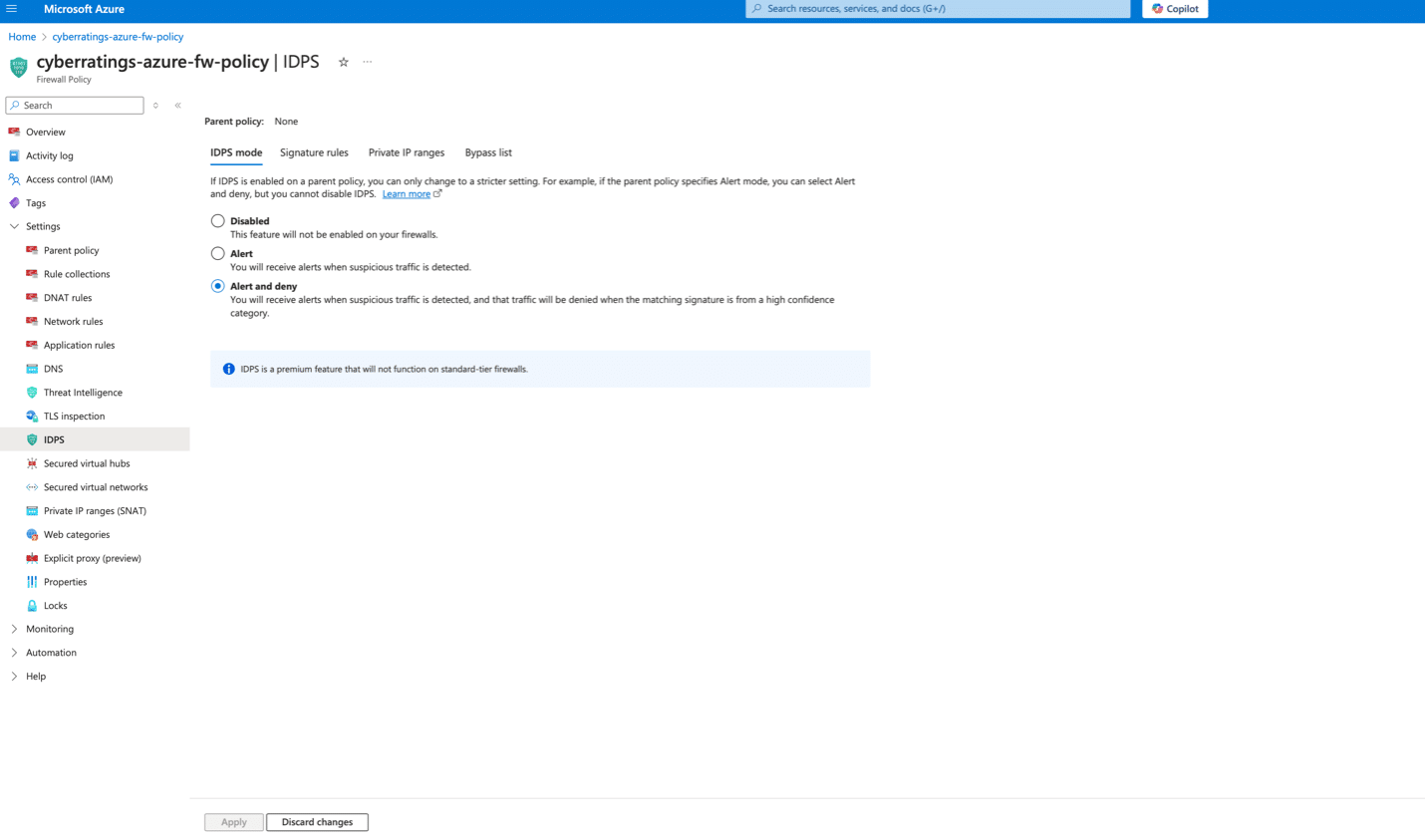
- Firewall Threat Intelligence Policy:

- Lastly, we set up logging and forwarded logs to NetWatcher, another service in Azure. The logs could then be analyzed in multiple formats.
CyPerf: https://github.com/Keysight/cyperf/tree/main/deployment/azure/terraform/controller_and_agent_pair
[1] https://cloud.google.com/firewall/docs/about-threats