Austin, TX – June 27, 2024 – CyberRatings.org (CyberRatings), the non-profit entity dedicated to providing confidence in cybersecurity products and services through its research and testing programs, has completed an independent test of eight market leading enterprise firewall vendors. Seven products were Recommended, and one received a Caution rating.
Enterprise firewalls are used to protect a trusted network from an untrusted network while allowing authorized communications to pass from one side to the other, thus facilitating secure business use of the Internet. Protection rate tests verified how effectively the firewall protected control network access, applications, and users while preventing threats (exploits and evasions), blocking malicious traffic under extended load, and remaining resistant to false positives.
Key Findings:
- When an exploit is blocked by a firewall, applying an evasion technique to that exploit is often easier for an attacker than finding a new exploit that isn’t blocked by that firewall.
- Threat actors apply evasion techniques to disguise and modify attacks to avoid detection by security products. Missing a type of evasion means a hacker can use an entire class of exploits to circumvent the security product. CyberRatings used multiple exploits for each evasion technique to see how each product defended against these combinations.
- Vendors have made progress towards “Secure by Default.” For the products and versions CyberRatings tested, if a vendor’s pre-defined high security configuration is selected, then firewall evasion defenses will be on by default. For other security configurations evasion defenses may not be enabled by default.
- Encryption matters: Roughly 80% of web traffic is encrypted. The top four cipher suites account for over 95% of HTTPS traffic. It should be noted that decryption is not on by default. Firewalls will not see attacks delivered via HTTPS unless configured to do so.
- Variants from well-known exploits are not always covered by vendors. At times, CyberRatings found multiple signatures/rules for the same Common Vulnerabilities and Exposures (CVE), with some offering more protection than others. Vendors may attempt to provide rapid coverage for high profile vulnerabilities by creating multiple exploit-specific signatures. If vendors don’t follow up with more comprehensive defenses, this approach can lead to gaps in protection.
To our knowledge, this was the most comprehensive evasion test performed to date. We have accelerated our research into evasion techniques as attackers increasingly bypass defenses,” said Vikram Phatak, CEO of CyberRatings.org. “An attacker can bypass protection if a firewall fails to detect a single form of evasion.”
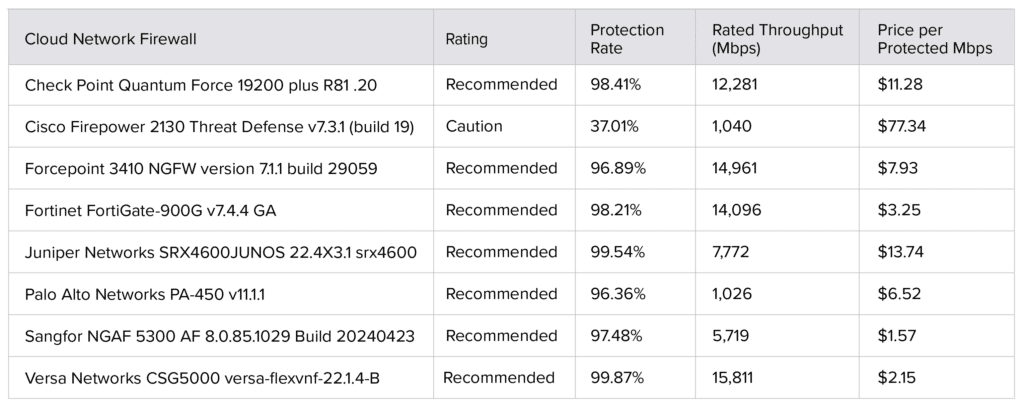
The following products were tested and rated:
Keysight provided their CyPerf and BreakingPoint tools to test performance, TLS functionality and stability. TeraPackets provided their Threat Replayer tool for packet replay, and CyberRatings used its own proprietary tools for live exploits and evasions.
The Enterprise Firewall Test Reports, Comparative and Security Value Map™ are available at CyberRatings.org.